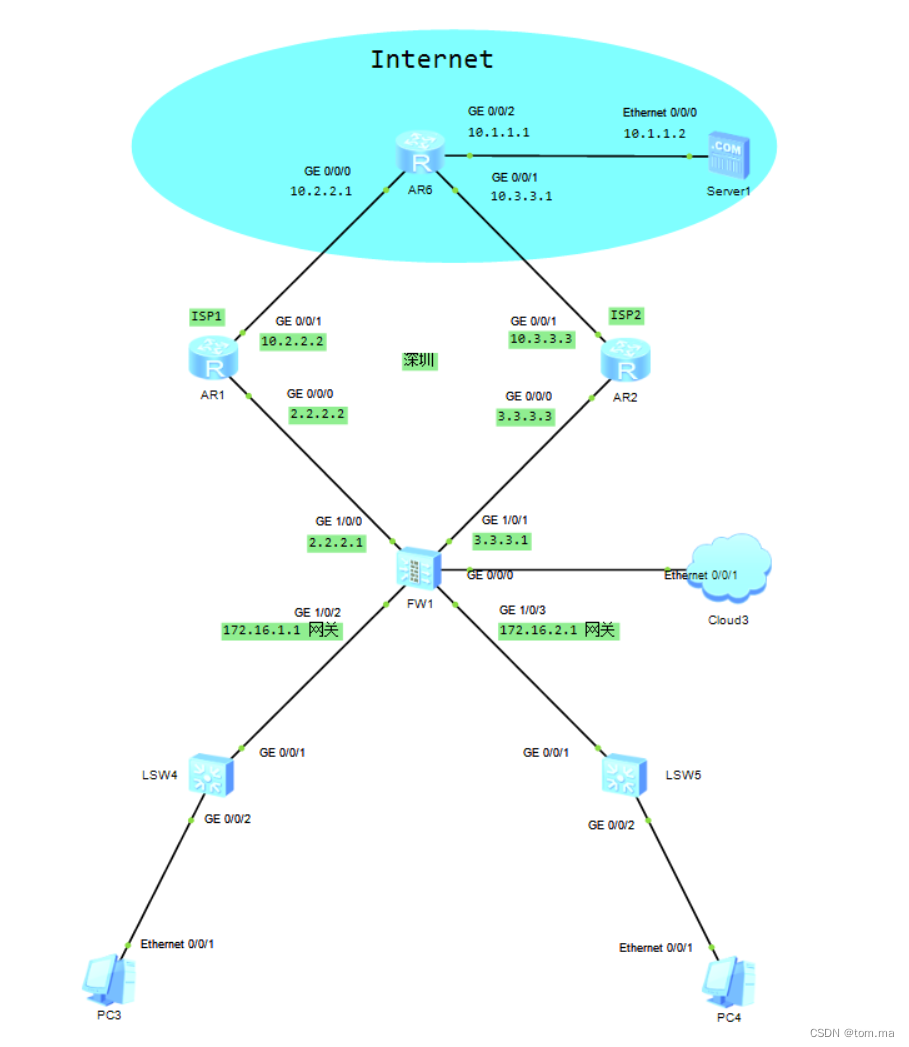
组网需求:
企业分别从ISP1和ISP2租用了一条链路
PC3用户上网访问Server1时走ISP1
PC4用户上网访问Server1时走ISP2
拓扑图
一、ISP1 运营商 R1路由器
<Huawei>sys [Huawei]sys R1 [R1]un in en [R1]int g0/0/0 [R1-GigabitEthernet0/0/0]ip addr 2.2.2.2 24 [R1-GigabitEthernet0/0/0]quit [R1]int g0/0/1 [R1-GigabitEthernet0/0/1]ip addr 10.2.2.2 24 [R1-GigabitEthernet0/0/1]quit # 配置OSPF [R1]ospf 1 [R1-ospf-1]area 0 [R1-ospf-1-area-0.0.0.0]network 10.2.2.0 0.0.0.255 [R1-ospf-1-area-0.0.0.0]network 2.2.2.0 0.0.0.255
二、ISP2 运营商 R2路由器
<Huawei>sys [Huawei]sys R2 [R2]un in en [R2]int g0/0/0 [R2-GigabitEthernet0/0/0]ip addr 3.3.3.3 24 [R2-GigabitEthernet0/0/0]quit [R2] [R2]int g0/0/1 [R2-GigabitEthernet0/0/1]ip addr 10.3.3.3 24 [R2-GigabitEthernet0/0/1]quit # 配置OSPF [R2]ospf 1 [R2-ospf-1]area 0 [R2-ospf-1-area-0.0.0.0]network 10.3.3.0 0.0.0.255 [R2-ospf-1-area-0.0.0.0]network 3.3.3.0 0.0.0.255
三、R6路由器
<Huawei>sys [Huawei]sys R6 [R6]un in en [R6]int g0/0/0 [R6-GigabitEthernet0/0/0]ip addr 10.2.2.1 24 [R6-GigabitEthernet0/0/0]quit [R6]int g0/0/1 [R6-GigabitEthernet0/0/1]ip addr 10.3.3.1 24 [R6-GigabitEthernet0/0/1]quit [R6]int g0/0/2 [R6-GigabitEthernet0/0/2]ip addr 10.1.1.1 24 [R6-GigabitEthernet0/0/2]quit # 配置OSPF [R6]ospf 1 [R6-ospf-1]area 0 [R6-ospf-1-area-0.0.0.0]network 10.1.1.0 0.0.0.255 [R6-ospf-1-area-0.0.0.0]network 10.2.2.0 0.0.0.255 [R6-ospf-1-area-0.0.0.0]network 10.3.3.0 0.0.0.255
四、防火墙
1、配置接口IP并加入相应的安全区域
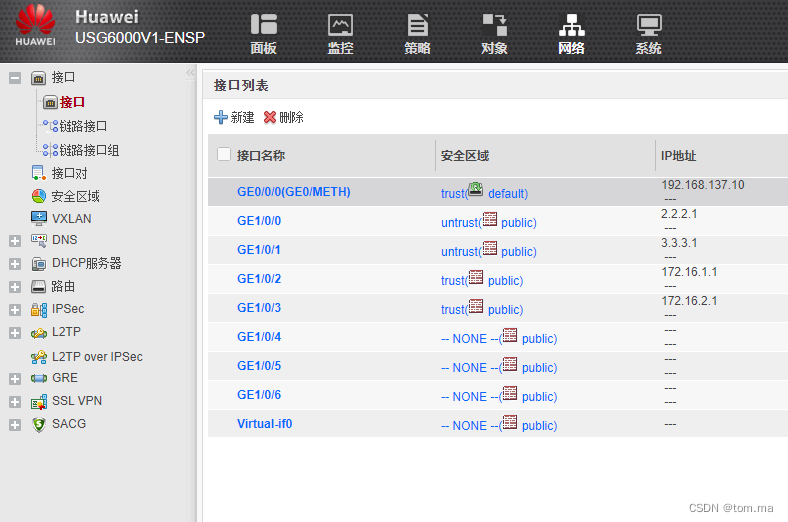
<USG6000V1>sys [USG6000V1]sys FW1 [FW1]un in en [FW1]dhcp enable # 桥接本地环回网卡,实现登陆WEB管理页面 [FW1]int g0/0/0 [FW1-GigabitEthernet0/0/0]undo ip addr 192.168.0.1 24 [FW1-GigabitEthernet0/0/0]ip addr 192.168.137.10 24 [FW1-GigabitEthernet0/0/0]service-manage all permit [FW1-GigabitEthernet0/0/0]quit [FW1]int g1/0/0 [FW1-GigabitEthernet1/0/0]ip addr 2.2.2.1 24 [FW1-GigabitEthernet1/0/0]service-manage all permit [FW1-GigabitEthernet1/0/0]quit [FW1]int g1/0/1 [FW1-GigabitEthernet1/0/1]ip addr 3.3.3.1 24 [FW1-GigabitEthernet1/0/1]service-manage all permit [FW1-GigabitEthernet1/0/1]quit [FW1]firewall zone untrust [FW1-zone-untrust]add int g1/0/0 [FW1-zone-untrust]add int g1/0/1 [FW1-zone-untrust]quit [FW1]int g1/0/2 [FW1-GigabitEthernet1/0/2]ip addr 172.16.1.1 24 [FW1-GigabitEthernet1/0/2]service-manage all permit [FW1-GigabitEthernet1/0/2]dhcp select int [FW1-GigabitEthernet1/0/2]quit [FW1]int g1/0/3 [FW1-GigabitEthernet1/0/3]ip addr 172.16.2.1 24 [FW1-GigabitEthernet1/0/3]service-manage all permit [FW1-GigabitEthernet1/0/3]dhcp select int [FW1-GigabitEthernet1/0/3]quit [FW1]firewall zone trust [FW1-zone-trust]add int g1/0/2 [FW1-zone-trust]add int g1/0/3 [FW1-zone-trust]quit
2、创建地址列表
[FW1]ip address-set 172.16.1.* type object [FW1-object-address-set-172.16.1.*]address 0 172.16.1.0 mask 24 [FW1-object-address-set-172.16.1.*]ip address-set 172.16.2.* type object [FW1-object-address-set-172.16.2.*]address 0 172.16.2.0 mask 24 [FW1-object-address-set-172.16.2.*]quit
3、配置安全策略
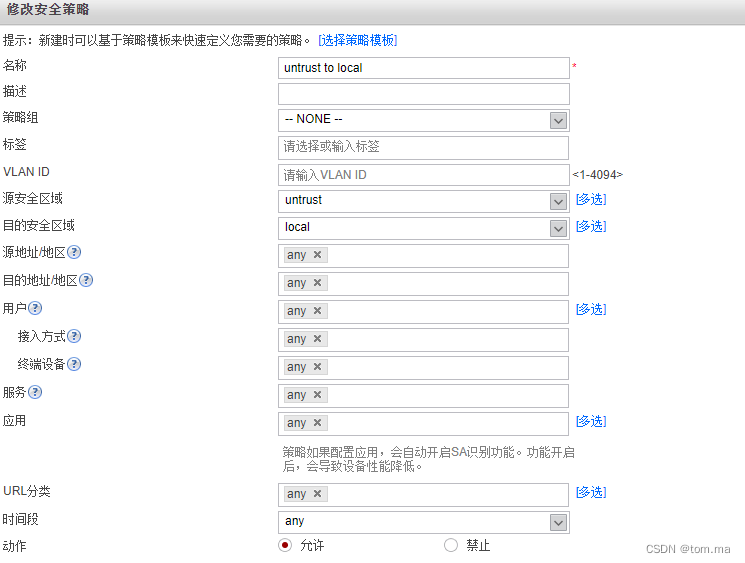
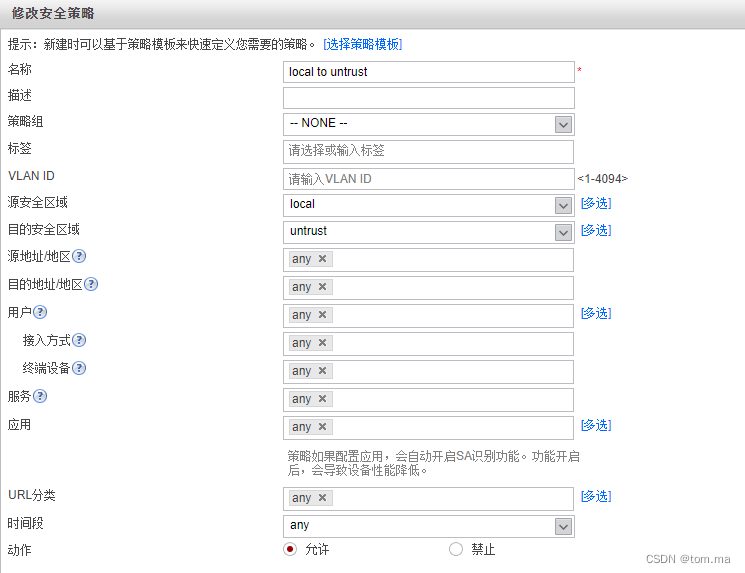
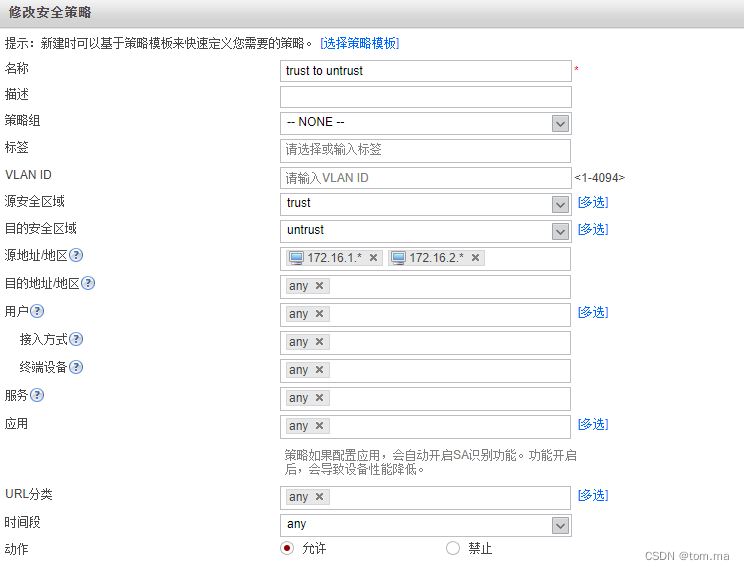
[FW1]security-policy [FW1-policy-security]rule name "untrust to local" [FW1-policy-security-rule-untrust to local]source-zone untrust [FW1-policy-security-rule-untrust to local]destination-zone local [FW1-policy-security-rule-untrust to local]action permit [FW1-policy-security-rule-untrust to local]rule name "local to untrust" [FW1-policy-security-rule-local to untrust]source-zone local [FW1-policy-security-rule-local to untrust]destination-zone untrust [FW1-policy-security-rule-local to untrust]action permit [FW1-policy-security-rule-local to untrust]rule name "trust to untrust" [FW1-policy-security-rule-trust to untrust]source-zone trust [FW1-policy-security-rule-trust to untrust]destination-zone untrust [FW1-policy-security-rule-trust to untrust]source-address address-set 172.16.1.* [FW1-policy-security-rule-trust to untrust]source-address address-set 172.16.2.* [FW1-policy-security-rule-trust to untrust]action permit [FW1-policy-security-rule-trust to untrust]quit
4、配置NAT策略
[FW1-policy-security]nat-policy [FW1-policy-nat]rule name "snat 1" [FW1-policy-nat-rule-snat 1]source-zone trust [FW1-policy-nat-rule-snat 1]egress-interface GigabitEthernet1/0/0 [FW1-policy-nat-rule-snat 1]source-address address-set 172.16.1.* [FW1-policy-nat-rule-snat 1]action source-nat easy-ip [FW1-policy-nat-rule-snat 1]rule name "snat 2" [FW1-policy-nat-rule-snat 2]source-zone trust [FW1-policy-nat-rule-snat 2]egress-interface GigabitEthernet1/0/1 [FW1-policy-nat-rule-snat 2]source-address address-set 172.16.2.* [FW1-policy-nat-rule-snat 2]action source-nat easy-ip [FW1-policy-nat-rule-snat 2]quit
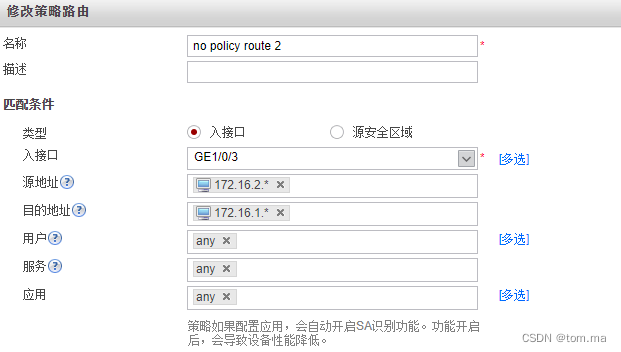
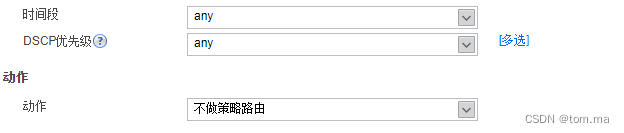
5、配置策略路由
[FW1]policy-based-route [FW1-policy-pbr]rule name "no policy route 1" 3 [FW1-policy-pbr-rule-no policy route 1]ingress-interface GigabitEthernet1/0/2 [FW1-policy-pbr-rule-no policy route 1]source-address address-set 172.16.1.* [FW1-policy-pbr-rule-no policy route 1]destination-address address-set 172.16.2.* [FW1-policy-pbr-rule-no policy route 1]action no-pbr [FW1-policy-pbr]rule name "no policy route 2" 4 [FW1-policy-pbr-rule-no policy route 2]ingress-interface GigabitEthernet1/0/3 [FW1-policy-pbr-rule-no policy route 2]source-address address-set 172.16.2.* [FW1-policy-pbr-rule-no policy route 2]destination-address address-set 172.16.1.* [FW1-policy-pbr-rule-no policy route 2]action no-pbr [FW1-policy-pbr-rule-no policy route 2]rule name "policy route 1" 1 [FW1-policy-pbr-rule-policy route 1]ingress-interface GigabitEthernet1/0/2 [FW1-policy-pbr-rule-policy route 1]source-address address-set 172.16.1.* [FW1-policy-pbr-rule-policy route 1]action pbr egress-interface GigabitEthernet1/0/0 next-hop 2.2.2.2 [FW1-policy-pbr-rule-policy route 1]rule name "policy route 2" 2 [FW1-policy-pbr-rule-policy route 2]ingress-interface GigabitEthernet1/0/3 [FW1-policy-pbr-rule-policy route 2]source-address address-set 172.16.2.* [FW1-policy-pbr-rule-policy route 2]action pbr egress-interface GigabitEthernet1/0/1 next-hop 3.3.3.3 [FW1-policy-pbr-rule-policy route 2]quit
6、配置OSPF
[FW1-policy-nat]ospf 1 [FW1-ospf-1]area 0 [FW1-ospf-1-area-0.0.0.0]network 2.2.2.0 0.0.0.255 [FW1-ospf-1-area-0.0.0.0]network 3.3.3.0 0.0.0.255 [FW1-ospf-1-area-0.0.0.0]network 172.16.1.0 0.0.0.255 [FW1-ospf-1-area-0.0.0.0]network 172.16.2.0 0.0.0.255
五、WEB 端查看
1、接口列表
2、安全策略
(1)untrust to local
(2)local to untrust
(3)trust to untrust
3、NAT策略
(1)snat 1
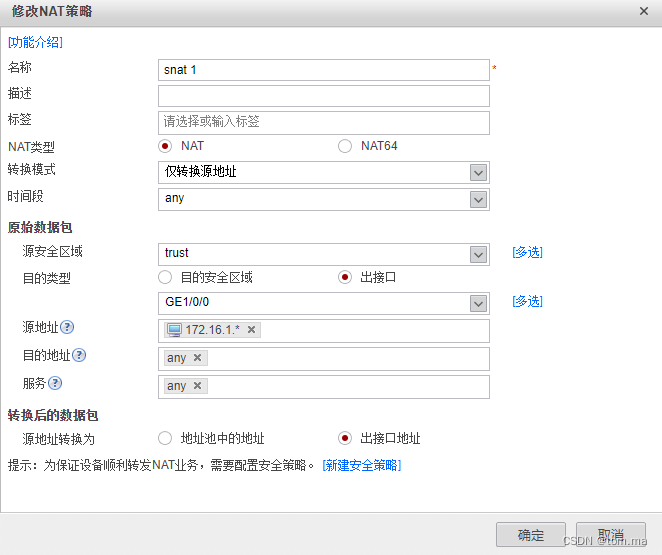
(2)snat 2

4、地址表

5、策略路由
(1)policy route 1

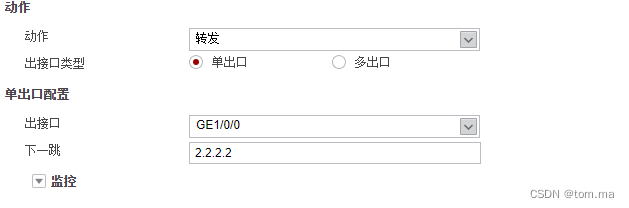
(2)policy route 2
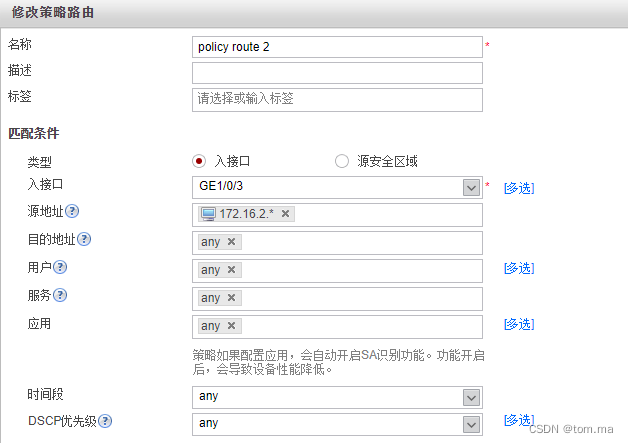

(3)no policy route 1


(4)no policy route 4
六、测试
1、PC3 访问 Server1
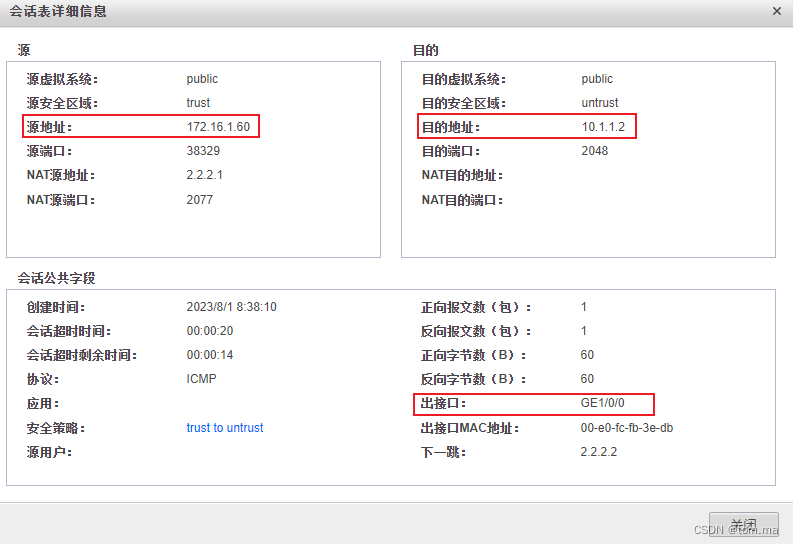
PC4 访问 Server1

通过上图分析得知,PC3 所在的172.16.1.0网段 访问 10.1.1.2 时出接口为 GE1/0/0。PC4 所在的172.16.2.0网段 访问 10.1.1.2 时出接口为 GE1/0/1
2、我们拿 PC3 访问 PC4,看下内网是否正常
PC3>ping 172.16.2.81 Ping 172.16.2.81: 32 data bytes, Press Ctrl_C to break From 172.16.2.81: bytes=32 seq=1 ttl=127 time=63 ms From 172.16.2.81: bytes=32 seq=2 ttl=127 time=62 ms From 172.16.2.81: bytes=32 seq=3 ttl=127 time=63 ms From 172.16.2.81: bytes=32 seq=4 ttl=127 time=46 ms From 172.16.2.81: bytes=32 seq=5 ttl=127 time=47 ms --- 172.16.2.81 ping statistics --- 5 packet(s) transmitted 5 packet(s) received 0.00% packet loss round-trip min/avg/max = 46/56/63 ms
我们发现是互通的,这里要注意一下,因为我已经在上面配置了 no pbr 不做策略路由,否则是不通的。 如果你的环境有 IPSecVPN 也需要做 no pbr
推荐本站淘宝优惠价购买喜欢的宝贝:
本文链接:https://www.hqyman.cn/post/7275.html 非本站原创文章欢迎转载,原创文章需保留本站地址!
打赏
 微信支付宝扫一扫,打赏作者吧~
微信支付宝扫一扫,打赏作者吧~

 微信支付宝扫一扫,打赏作者吧~
微信支付宝扫一扫,打赏作者吧~休息一下~~


