<code class=" language-bash"><span class="token punctuation">[root@director-A ~<span class="token punctuation">]<span class="token comment">
Chain INPUT <span class="token punctuation">(policy ACCEPT 0 packets, 0 bytes<span class="token punctuation">)
pkts bytes target prot opt <span class="token keyword">in out <span class="token function">source destination
471 44874 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate RELATED,ESTABLISHED
192 14016 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0
19 1456 INPUT_direct all -- * * 0.0.0.0/0 0.0.0.0/0
19 1456 INPUT_ZONES_SOURCE all -- * * 0.0.0.0/0 0.0.0.0/0
19 1456 INPUT_ZONES all -- * * 0.0.0.0/0 0.0.0.0/0
0 0 DROP all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate INVALID
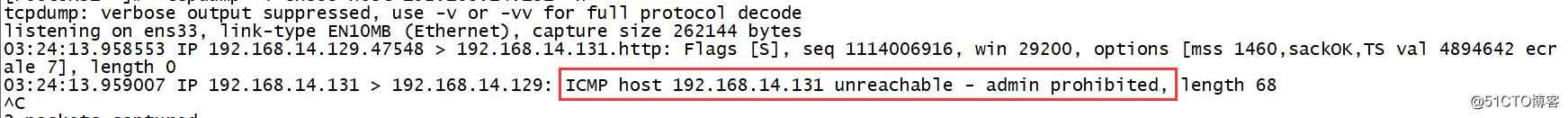
18 1404 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited <span class="token comment">
<span class="token punctuation">[root@director-B ~<span class="token punctuation">]<span class="token comment">
Chain INPUT_direct <span class="token punctuation">(1 references<span class="token punctuation">)
pkts bytes target prot opt <span class="token keyword">in out <span class="token function">source destination
<span class="token punctuation">[root@director-B ~<span class="token punctuation">]<span class="token comment">
Chain INPUT_ZONES_SOURCE <span class="token punctuation">(1 references<span class="token punctuation">)
pkts bytes target prot opt <span class="token keyword">in out <span class="token function">source destination
<span class="token punctuation">[root@director-B ~<span class="token punctuation">]<span class="token comment">
Chain INPUT_ZONES <span class="token punctuation">(1 references<span class="token punctuation">)
pkts bytes target prot opt <span class="token keyword">in out <span class="token function">source destination
55 4210 IN_public all -- ens33 * 0.0.0.0/0 0.0.0.0/0 <span class="token punctuation">[goto<span class="token punctuation">]
0 0 IN_public all -- + * 0.0.0.0/0 0.0.0.0/0 <span class="token punctuation">[goto<span class="token punctuation">]
<span class="token punctuation">[root@director-B ~<span class="token punctuation">]<span class="token comment">
Chain IN_public <span class="token punctuation">(2 references<span class="token punctuation">)
pkts bytes target prot opt <span class="token keyword">in out <span class="token function">source destination
28 2158 IN_public_log all -- * * 0.0.0.0/0 0.0.0.0/0
28 2158 IN_public_deny all -- * * 0.0.0.0/0 0.0.0.0/0
28 2158 IN_public_allow all -- * * 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 <span class="token comment">
<span class="token punctuation">[root@director-B ~<span class="token punctuation">]<span class="token comment">
Chain IN_public_log <span class="token punctuation">(1 references<span class="token punctuation">)
pkts bytes target prot opt <span class="token keyword">in out <span class="token function">source destination
<span class="token punctuation">[root@director-B ~<span class="token punctuation">]<span class="token comment">
Chain IN_public_deny <span class="token punctuation">(1 references<span class="token punctuation">)
pkts bytes target prot opt <span class="token keyword">in out <span class="token function">source destination
<span class="token punctuation">[root@director-B ~<span class="token punctuation">]<span class="token comment">
Chain IN_public_allow <span class="token punctuation">(1 references<span class="token punctuation">)
pkts bytes target prot opt <span class="token keyword">in out <span class="token function">source destination
1 52 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:22 ctstate NEW <span class="token comment">








 微信支付宝扫一扫,打赏作者吧~
微信支付宝扫一扫,打赏作者吧~